EU Directive NIS2 – how to prepare your company for changes?

The NIS2 Directive (Network and Information Systems Directive 2) must enter into force in Polish law no later than October 17, 2024. The main purpose of the NIS2 Directive is to define the minimum provisions that Member States should implement to reduce the risk of cybersecurity incidents.
NIS2 encourages Member States to introduce regulations that will require supply chain demonstration, vulnerability management, basic internet services, and the application of cyber hygiene principles. Automation and monitoring of IT infrastructure will be essential practices that will significantly facilitate and reduce the workload of the NIS2 directive implementation process, especially since maintaining compliance with NIS2 is a continuous process.
In today’s complex IT world, we cannot do without tools for continuous monitoring and automatic detection of vulnerabilities, tracking incidents, as well as optimizing the environment, measuring performance, costs and maintaining compliance with policies for maintaining a healthy, i.e. safe, data processing environment. On the other hand, the multitude and specificity of tools often necessitate the use of many tools. VMware, a leading provider of data processing platforms in the public cloud and data center (private cloud), has monitoring and automation solutions that can constitute single points of supervision over the entire IT, taking into account the security aspects of various domain tools.
INDEVOPS specializes in implementing monitoring and automation solutions using VMware products. INDEVOPS activities respond to the needs of monitoring and orchestration of the complete IT area, from hardware to applications, from data centers through remote units to the public cloud, implementing solutions in small and medium-sized enterprises as well as the largest companies in Poland.
What is NIS2?
The NIS2 Directive (Network and Information Systems Directive 2) entered into force on January 16, 2023. We now have 21 months to implement it into national law. Currently, the Act of July 5, 2018 on the national cybersecurity system is in force, which requires amendment due to changes in NIS2. On July 11, parliamentary committees decided to hold a public hearing on this project. As of October 16, 2023, work is still ongoing, which means that without an amendment to the KSC Act, NIS2 cannot yet be used. However, time passes and it is worth familiarizing yourself with the purpose and requirements of this directive, which must enter into force in Polish law no later than October 17, 2024.
The topic of cybersecurity is very important in the European Union. Following an audit of the functioning of the directive introduced in 2016, it turned out that Member States were implementing EU rules in this area, but to varying degrees. Therefore, the main objective of the NIS2 Directive is to define the minimum provisions that Member States should implement to reduce the risk of cybersecurity incidents. In addition, NIS2 requires updating sectors and activities, introducing corrective measures and enforcement measures. We will all benefit from the introduction of these regulations and the harmonization of minimum provisions, and the greatest financial relief will be felt by companies that offer cross-border services and have to deal with differences between countries in the field of cybersecurity.
Is NIS2 just a whim of the European Commission or are there benefits from its use?
Looking at the provisions and requirements of the directive, the only thing that member states will be “forced” to do is to increase the level of security, because so far countries have had different approaches to it. In the “cyber” world, this approach is especially appropriate. The specific benefits of applying the NIS2 directive include:
- increasing resistance to cyber threats;
- increasing the ability to respond to cybersecurity incidents and crises;
- increasing awareness and education in the field of cybersecurity among citizens and entities;
- increasing the protection of fundamental rights and the security of personal data in cyberspace (GDPR);
- increasing trust in the digital internal market and the competitiveness of European digital entities.
Which entities need to implement NIS2?
Entities will be obliged to take measures to increase the level of cybersecurity:
- cross-border service providers, such as DNS and TLD registry providers, domain name registration providers, cloud providers, edge computing and data center services (referred to as core internet services);
- from sectors important for the economy and society, e.g. energy, transport, banking, financial market infrastructure, health care, drinking water, waste, chemical and nuclear production;
- from digital sectors, e.g. social media service providers, data sharing services, content sharing services, internet search services and email services.
An important fact is that the NIS2 directive encourages Member States to introduce regulations that will require the demonstration of the supply chain, i.e. the identification of all entities involved in the provision of cyberspace-related products or services, such as manufacturers, suppliers, distributors, integrators, operators or end users. Therefore, entities will have to demonstrate all elements used in data processing, both internal and external.
Size or importance of the enterprise?
The provisions of the NIS2 directive will have to be implemented by large and medium-sized enterprises, and other entities (even small or micro-enterprises) – if they meet specific criteria indicating a key role for society, the economy or specific sectors and types of services. It is worth consulting with people responsible for legal services now to assess whether and to what extent your company is subject to NIS2 requirements.
It is worth adding that the NIS2 directive stipulates that the risk management measures implemented and their costs should be proportional to the entity, without imposing too high administrative and financial burdens on entities.
Cyber hygiene – prevention is better than cure

The slogan “prevention is better than cure” is also important in cybersecurity and refers to the application of cyber hygiene principles – a set of good practices: behaviors and measures that are able to prevent cyber threats. This concerns the protection of network infrastructure and IT systems, the security of hardware, software and Internet applications, and the protection of company and end-user data.
On the one hand, these requirements will include the purchase of appropriate products and services, and on the other – documenting, training and providing regular training to employees, e.g. regarding the recognition, assessment and management of cybersecurity risks. In addition to efficient (up-to-date) ICT systems, it is important to build awareness and educate employees of entities using NIS2D in the field of cybersecurity. Trained and aware of cyber threats employees will guarantee quick and correct threat identification and then cyber security risk management.
Risk management measures
Risk management measures referred to in Art. 21 of the NIS2 directive, are divided into technical, operational and organizational and concern the following aspects of cybersecurity:
a) risk analysis and security policies for IT systems;
b) handling the incident: detecting, reporting and documenting its course to repairing its effects;
(c) business continuity, e.g. backup management and emergency recovery, and crisis management;
(d) supply chain security, including security aspects relating to the relationship between each entity and its direct suppliers or service providers;
e) security in the process of acquiring, developing and maintaining networks and IT systems, including dealing with vulnerabilities and their disclosure;
(f) policies and procedures to assess the effectiveness of cybersecurity risk management measures;
g) basic cyber hygiene practice and cybersecurity training;
(h) policies and procedures for the use of cryptography and, where appropriate, encryption;
i) human resources security, access control policy and asset management;
(j) where appropriate, the use of multi-factor or continuous authentication, secure voice, text and video calls and secured intra-entity communications systems in emergency situations.’
This list can be summarized as a typical “arsenal” of selected safeguards described in the ISO 27001 standard, in Annex A. It is worth adding here that the NIS2 directive does not impose or favor any of the technologies, although it indicates standardization (Article 25 ) as a way to support the consistent implementation of cybersecurity management measures. In our opinion, if an entity uses standardization, it has already developed habits similar to standardization under Art. 25 NIS2, and standardization often coincides with the legal requirements for standardization, which makes these concepts identical.
NIS2 also includes a provision that the risk management measures implemented and their cost should be proportional to the entity, without imposing excessive administrative and financial burdens on entities. To determine this, a risk analysis is used, which is based, among others, on: on the current state of knowledge regarding risk management measures and the cost of their implementation. Such a task will probably be assigned to people handling purchasing processes in the organization. The NIS2 directive also introduces the responsibility of company management for compliance with cybersecurity risk management measures.
Are you sure your company maintains cyber hygiene? If not, please contact us and click ” here “.
Can you stop a cybercriminal attack?
Unfortunately, we will not be able to stop cybercriminal attacks. However, if the entity takes the implementation of the NIS2 directive seriously, it will be possible to stop most attacks. If we apply cyber hygiene and apply the above-mentioned “arsenal” of selected security measures described in the ISO 27001 standard will minimize the risk of a successful attack to zero.
Why is it worth monitoring your IT environment? One of the requirements specified in Art. 21 of the NIS2 Directive is to ensure business continuity by anticipating, preventing and resolving problems in the cloud or across multiple clouds, from applications to infrastructure.
It used to be that an IT specialist could notice and respond to cyber intrusions by observing messages or images from monitoring systems. This approach worked well with a small number of cyberattacks and when using a few applications. Today this approach is not sufficient. In the case of our clients, the number of applications (business services) ranges from a dozen to several dozen. Each service has a minimum of 2 components (application and database). In addition, services (including components) have production and development versions (environments), and often also “PREPROD”, “TST” and others. These also include remote locations where these services must be present, or public cloud environments where these services are placed. The vast majority of these services communicate with each other and also communicate with external services and third-party vendor services. The number of operating systems on which these “applications” run ranges from several hundred to several thousand. In INDEVOPS alone , we have over 250 instances of operating systems, and in the development environment, automatic tests create and decommission several hundred systems a day.
Moreover, today’s cybercriminals are increasingly less likely to attack IT environments from outside. Attacks from inside the network turn out to be more effective because the first step to overcome is the user: “Good morning, Mr. Radosław, I’m calling you from the helpdesk, I need your e-mail password because I need to reset it,” or: “Good morning, I’m from helpdesk I came to replace a computer” (the example is used during an audit during which an accounting auditor connected his computer to the network and carried out an attack on an unsecured Microsoft SCCM server and gained control over the organization’s Active Direcotry).
The next steps of the attack use “traditional” technical methods that exploit vulnerabilities in the software (errors, obsolescence, incorrect configuration). It turns out that inside the organization, IT systems are no longer so strongly protected in terms of security. Interestingly, cyber intrusions are not revolutionary, e.g. stealing or blocking sensitive (business-valuable) data, using the attacked environment for another attack or using additional computing power.
To summarize, the answer to the question “is it worth monitoring?” is obvious. However, the thought comes to mind that this question should be changed to “how to monitor effectively”?
How to monitor the IT environment?
Given the number of systems or applications currently used in large IT environments, several monitoring tools are currently used. Each tool is dedicated to specific scopes of operation, e.g.: · scans computer networks for security vulnerabilities, unknown or outdated systems, · collects system and application logs, · tracks traces and metrics, · supports the vulnerability management process, where after identification the repair business process will be carried out, · monitors a given IT layer, e.g. applications, virtual environment, computer networks. Unfortunately, the use of many tools means that monitoring is treated as an island, without a unified view of the whole, and there are no connections between elements, different types of data or objects. This does not effectively prevent failures, although their detection works correctly. In the event of a failure, repair time is significantly extended and the repair process is time-consuming, not to mention the difficulty in determining the root cause of the problem.
It is necessary to use tools that can aggregate data from all sources and “look” at the environment from the user’s entry point to the place where the data the user uses is stored. However, the entire environment should be globally analyzed in terms of any anomalies occurring in it. For this purpose, “machine learning” engines can be used, operating on large sets of structured (metrics) and unstructured data (logs, events). ML engines can learn the behavior of the environment and respond to something that was not there before.
Today’s global monitoring is called Observability and allows you to observe systems, applications, network devices, user devices, on-premises and cloud resources. The goal is to capture everything and everywhere, both to see the user’s journey in every place of the IT stack and to show the view from the business side, e.g. how many orders does a given service (business application) complete per hour?
Observability can be implemented by one monolithic system, but may be the result of coupled operation of systems, e.g. a system that monitors itself can integrate with many domain systems (e.g. for application monitoring, data center monitoring, monitoring network devices of a given manufacturer, etc. .) and provide top-down visibility into the entire IT environment.
Example features of the Observability tool:
1. Observe complete IT stacks, from hardware to services, in on-premises data centers and public clouds.
- the tool uses plug-ins to connect elements of the IT environment, which enables monitoring of any types of traditional and cloud IT elements, in particular it enables integration with domain systems, e.g. Data Center Infrastructure Management, Building Systems Management, Security Scanner, etc., and even other monitoring systems;
- The plugin system is open and allows you to build plugins yourself, also using a no-code tool.
The INDEVOPS team itself created plug-ins for Cisco, Juniper, CheckPoint computer network devices and IBM and Broadcom (Brocade) data storage devices:
- computer network switches and routers, Juniper;
- computer network firewall, CheckPoint;
- computer network switches and access points, Cisco;
- disk arrays, IBM XIV;
- SAN switches, Brocade (Broadcom).
2. Discovering connections and topologies in the IT environment:
- the tool discovers the types of connected elements and their components, e.g. ports, instances, metrics and parameters, and also draws connections between elements and their components depending on their actual relationship, e.g. what virtual machine is the application on?, on what disk areas are they placed virtual machines?, what ports are on the network switch?, what disks are exposed from the disk array?, what databases are in the database engine instance?, what application instances constitute applications and on what systems are they running?
- discovery is automatic, although it is possible to manually or semi-automatically build connections based on applied naming schemes or tags.
3. Insights into structured and unstructured data:
- the tool has engines for structured and unstructured data that are adapted to a given type of data, and on the other hand, it enables the linking of structured and unstructured data of a given object for the purposes of uniform alerting,
- Additionally, it automatically structures unstructured data to enable tracking in a way similar to metrics, and performs analyzes on them enabling automatic grouping into applications, detection of attack signatures or operational detection of irregularities.
4. A common view of the entire IT environment:
- the tool provides one central system of views that can be assigned to selected recipients (also outside the organization) and adapted to your own needs by modifying or creating your own views from scratch, although it has predefined views for troubleshooting, capacity, performance, cost and optimization and energy consumption, including CO2 reduction (sustainability),
- views provide standardized insight into relationships, metrics, predictions, parameters, alerts and symptoms of all monitored elements regardless of their type, as well as hooking up external elements for a unified user experience and redirecting to domain tools if deeper analysis is needed.
5. Resource optimization and planning for performance, capacity and costs:
- based on the stored history, the tool builds behavioral trends and calculates automatic thresholds for each metric of each monitored object, which allows predicting behavior and introducing recommendations on various subsets defined in the tool (entire data centers, groups of systems, defined business applications, in terms of migration, transfer , increasing resources and recovering them in case of too low utilization, e.g. recovering unused RAM, searching for abandoned resources,
- enables calculation of data center costs with definitions of own rates for hardware and software costs and comparison with public cloud costs in the case of load transfer (deeper analysis through integration with the CloudHealth tool).
6. Advanced alerting and reporting:
- instead of alerting based on exceeded thresholds, the tool uses symptom-based alerting, in which an abnormality is indicated by one or more symptoms that constitute an alert (important: symptoms can occur without creating an alert), both of which have their own independent priorities and recommendations that operators can use to solve problems,
- alerting uses automatic trends and thresholds, thanks to which it is possible to detect unexpected increases in load in one or more systems, which may indicate an attack or intrusion,
- alerting has predefined report templates, with the ability to create individual reports from any selected elements, as well as export to PDF and XLSX and automatic sending by e-mail.
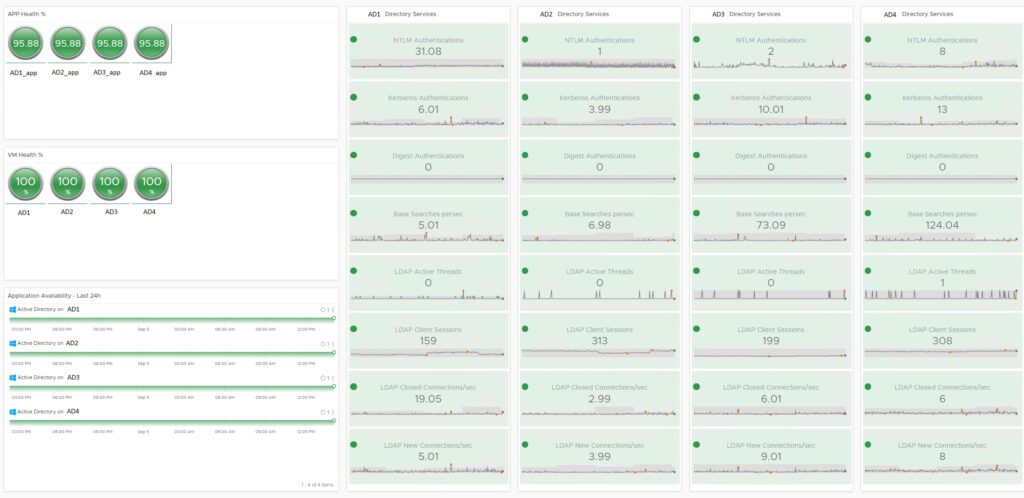
7. Monitoring business services and SLA:
- the tool has universal metrics with percentage values for each monitored element, which allows you to compare different types of elements (e.g. virtual machine and power supply) and build them into logical containers constituting sets of elements and representing components, in particular business services, enabling simple health monitoring and SLA of these components (services),
- A special case is the ability to create views of recipients and service providers by building containers for different IT layers, different areas and locations.
8. Verification of monitored elements for security compliance:
- built-in compliance policy mechanism for various types of monitored objects, integrated with the alerting and reporting mechanism, with default policies for checking compliance with regulations and policies for VMware vSphere, NSX-T, vSAN infrastructure and international CIS regulations, DISA, FISMA, HIPAA, ISO and PCI. The mechanism also allows you to create your own “Custom Compliance” standards for compliance monitoring.
Analyzing the security of the IT system, maintaining business continuity and assessing the effectiveness of already implemented measures becomes crucial for the implementation of NIS2. For this purpose, it is important, in accordance with the ISO19011 standard for auditing management systems, that the company has the appropriate amount of information which, after analysis, will become audit evidence. On their basis, the auditor will make audit findings, deciding on compliance or non-compliance with the standards in the NIS2 directive. System with the above set of features is able to support the entity in the business aspect of monitoring its IT environment, but will also provide information that will be useful in implementing and maintaining NIS2.
How does INDEVOPS support companies in implementing NIS2 requirements?
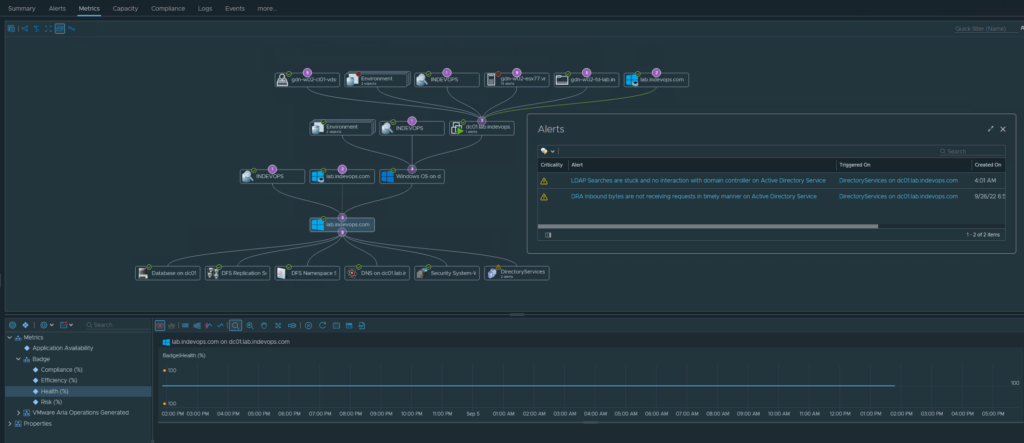
INDEVOPS fulfills the described roles for an integrator in the supply chain and performs necessary tasks for an entity covered by the requirements of the NIS2 directive. The company was established in 2017 to specialize in monitoring and automation of the maintenance of IT infrastructure and services. It provides its services based on its own expert experience gained during several years of working with IT systems, using VMware Aria Operations software, on the example of which the features of the system enabling the implementation of the Observability idea were described, by equipping it with third-party extensions and proprietary plug-ins developed in cooperation with technological partners, extending the capabilities of the Aria Operations tool to monitor a complete set of IT infrastructure layers:
- VMware Network Insight – application network security analysis along with mechanisms for detecting network anomalies through network flows (Netflow)
- Flopsar – insight into applications, in line with the Application Performance Monitoring trend,
- UptimeDC – monitoring data center elements (so-called Data Center Inventory Management),
- Greenbone – so-called security scanning Security Scanner.
Additionally, INDEVOPS , by implementing other VMware solutions, can help you meet the new NIS2 security requirements. Below is a list of solutions:
- VMware Carbon Black – a cloud-based endpoint protection platform that provides advanced threat detection and prevention, user and device behavior analysis, threat isolation and removal, and integration with other security systems,
- VMware Workspace ONE/Inteligent/Mobile Threat Defense – a digital workplace management platform that enables you to securely deliver and manage any application on any device, wherever it is, using multi-factor authentication, conditional access and single sign-on.
- VMware NSX Advanced Threat Prevention – a network virtualization and security platform that is a collection of analytical tools designed to defend against advanced threats that use known and unknown attack vectors. It enables full inspection of network traffic and detects and prevents known threats such as ransomware, malware, command-and-control communications, lateral traffic attempts and data theft. It uses artificial intelligence (AI) and machine learning (ML) to analyze advanced threats and quickly respond to them. It also offers comprehensive visibility of both north-south and east-west traffic, including an overview of abnormal behavior
- VMware Cloud Disaster Recovery – a solution for quick and effective recovery from a failure or ransomware attack in the VMware cloud

Summary
In the implementation of the NIS2 directive, monitoring the IT infrastructure becomes necessary to verify compliance with its requirements. By providing up-to-date data on the state of IT systems, these technologies can help organizations meet the requirements of the directive and increase their overall level of cybersecurity. However, in today’s complex and extensive environments, a modern system implementing the idea of Observability is able to significantly increase the level of observation by automatically detecting non-standard behaviors coming from many sources, using machine learning mechanisms. This allows us to optimize the environment, measure performance, costs and compliance with our policies, regardless of whether the data is processed in our data center or in a public cloud.
The role of INDEVOPS is to ensure the security of solutions delivered to entities that will be covered by the guidelines of the NIS2 directive, technical support ensuring business continuity, training of Customer Employees, as well as ensuring that the solutions delivered to the Customer, as well as the form of cooperation between the entity and the supplier, are consistent with regulations. INDEVOPS supports its clients in performance optimization, capacity management, cost management, event management, compliance with guidelines and reporting on various system elements.
INDEVOPS is the only VMware partner originating from Poland that has a service partnership (Master Services Competency) at the Principal level, as well as a cloud provider partnership (Cloud Services Provider) and a Technology Alliance – Standard software developer partnership. Within EMEA, we are the only subcontractor of DellEMC in Operations and Automation. Since 2017, we have been providing key solutions to clients, including renowned companies such as PKN Orlen, ING Tech, Poczta Polska, Inpost, Alior, PERN, PCSS, MBank, Polkomtel, Polpharma and many others.
INDEVOPS has over 30 leading clients and hundreds of users using the solutions we provide. We cooperate with partners such as VMware, DellEMC, Bluemedora, NetFlow Logic and Greenbone, which guarantees the highest quality of our services.
Please contact us if you want more information, please click HERE
Sources:
https://eur-lex.europa.eu/legal-content/PL/TXT/PDF/?uri=CELEX:32022L2555&qid=1697431135136 , p. 48, art. 21 (accessed on October 16, 2023)
https://www.vmware.com/ (accessed on October 17, 2023)
https://docs.vmware.com/en/VMware-Aria-Operations/index.html (accessed on October 16, 2023)
https://www.vmware.com/products/aria-operations.html
The authors would like to thank Krzysztof Kowalski for source materials on the NIS2 directive and Ewa Szymczak for coordinating the work and the marketing campaign.